ISAKMP Phase 1 (IKE)
This is a 2-step process:
1. configure ISAKMP policy
IKE configuration (ISAKMP policy) is universally applicable. That means this set of configurations will be tried with every IPSec peer this router has.
2. Define Peer router IP with a pre-shared key
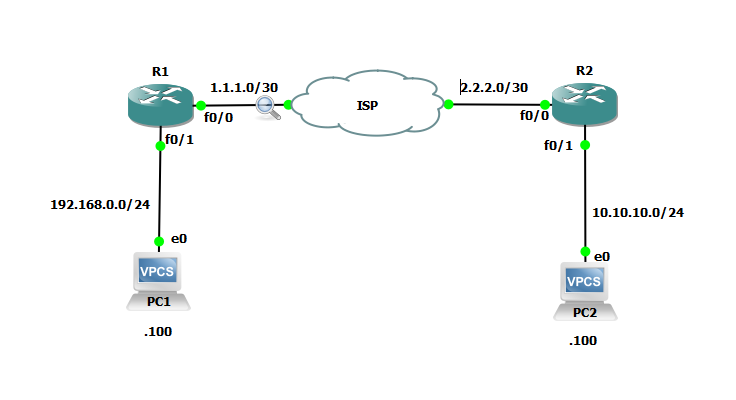
crypto isakmp policy 1 encr aes 256 hash sha512 authentication pre-share group 24 lifetime 300 crypto isakmp key IPSec-key address 2.2.2.2
ISAKMP Phase 2 (IPSec)
This is a 4-step process:
1. Create IPSec transform set
2. Create ACL to identify interesting traffic to be VPNed
3. Create Crypto MAP
4. Apply the Map to our public interface
crypto ipsec transform-set T-SET esp-gcm 256 mode tunnel >>>>>> tunnel mode is by default. so you dont have enter this command ip access-list extended VPN-ALLOWED-TRAFFIC permit ip 192.168.0.0 0.0.0.255 10.10.10.0 0.0.0.255 crypto map C-MAP 10 ipsec-isakmp set peer 2.2.2.2 set transform-set T-SET match address VPN-ALLOWED-TRAFFIC interface FastEthernet0/0 ip address 1.1.1.1 255.255.255.252
crypto map C-MAP
As soon as you enter the last command you will see IPsec tunnel is turning ON:
R2(config-if)#crypto map C-MAP
R2(config-if)#
*Sep 20 23:32:15.867: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
Verification
R1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
2.2.2.2 1.1.1.1 QM_IDLE 1002 ACTIVE
R1#show crypto session
Crypto session current status
Interface: FastEthernet0/0
Session status: UP-NO-IKE
Peer: 2.2.2.2 port 500
IPSEC FLOW: permit ip 192.168.0.0/255.255.255.0 10.10.10.0/255.255.255.0
Active SAs: 2, origin: crypto map
