Configuration on Cisco
It is a 7-step process on a Cisco router. The steps are:
- Turn ON HTTP server on R1
- Turn R1 into a CA so that it can create client certificates
- Create client certificate on R1
- Configure AAA
- Configure IKEv2
- Configure IPSec
- Create virtual-template1 and bind the IPSec profile to it.
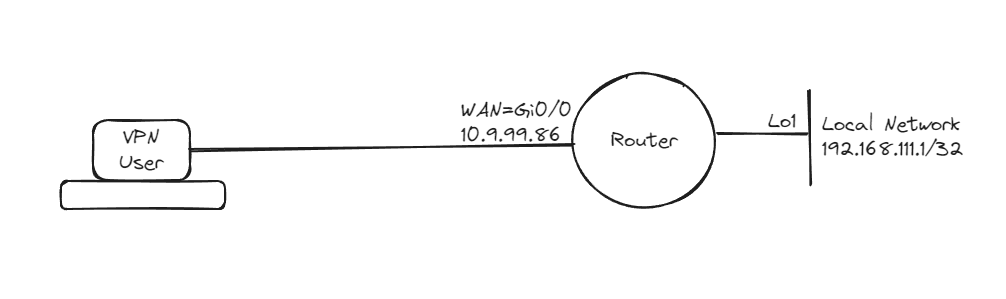
Pre-configuration
hostname R1
no ip domain lookup
interface Loopback1
ip address 192.168.111.1 255.255.255.255
interface GigabitEthernet0/0
ip address 10.9.99.86 255.255.255.0
no shutdown
username reashad privilege 15 password FlexVPN-p@ssword
line vty 0 4
privilege level 15
logging synchronous
login local
transport input ssh
FLEXVPN configuration
=============================================
1.Turn ON HTTP server:
ip http server
=============================================
2.Turn R1 into a CA so that it can create client certificates:
crypto pki server R1-CA
issuer-name cn=”R1-CA”
grant auto
no shutdown
=============================================
3.Create client certiface on R1:
3.1 configure domain
ip domain name reashad.com
3.2 Create trustpoint and enrollment URL:
crypto pki trustpoint R1-CLIENT
enrollment url http://10.9.99.86
subject-name cn=R1-CLIENT.com.reashad
3.3 Accept the certificate:
crypto pki authenticate R1-CLIENT
3.4 Finally create the client certificate:
crypto pki enroll R1-CLIENT
=============================================
4. Configure AAA
aaa new-model
aaa authentication login A-EAP-AUTHEN-LOCAL local
aaa authorization network A-EAP-AUTHOR-GRP local
=============================================
5. IKEv2:
5.1 IKEv2 authorization policy:
crypto ikev2 authorization policy IKEV2-AUTH-POLICY
pool ACPOOL
dns 1.1.1.1
def-domain reashad.com
route set remote ipv4 192.168.111.1 255.255.255.255
5.2 Create the pool:
ip local pool ACPOOL 192.168.10.5 192.168.10.10
5.3 IKEv2 Proposal
crypto ikev2 proposal IKEV2-PROP1
encryption aes-cbc-256
integrity sha256
group 19
5.4 IKEv2 Policy:
crypto ikev2 policy IKEV2-POL
proposal IKEV2-PROP1
5.5 IKEv2 Profile:
crypto ikev2 profile AnyConnect-EAP
match identity remote key-id *$AnyConnectClient$*
authentication local rsa-sig
authentication remote anyconnect-eap aggregate
pki trustpoint R1-CLIENT
aaa authentication anyconnect-eap A-EAP-AUTHEN-LOCAL
aaa authorization group anyconnect-eap list A-EAP-AUTHOR-GRP IKEV2-AUTH-POLICY
virtual-template 1
=============================================
6. IPSec:
6.1 IPSec transform set:
crypto ipsec transform-set TS esp-aes 256 esp-sha256-hmac
6.2 Create IPSec profile:
crypto ipsec profile AnyConnect-EAP
set transform-set TS
set ikev2-profile AnyConnect-EAP
=============================================
7. Create virtual-template1 and bind the IPSec profile to it:
interface Virtual-Template1 type tunnel
ip unnumbered Loopback1
ip mtu 1400
tunnel mode ipsec ipv4
tunnel protection ipsec profile AnyConnect-EAP
Windows configuration
1. Install these 2 files

2. Open VPN profile editor and create your profile
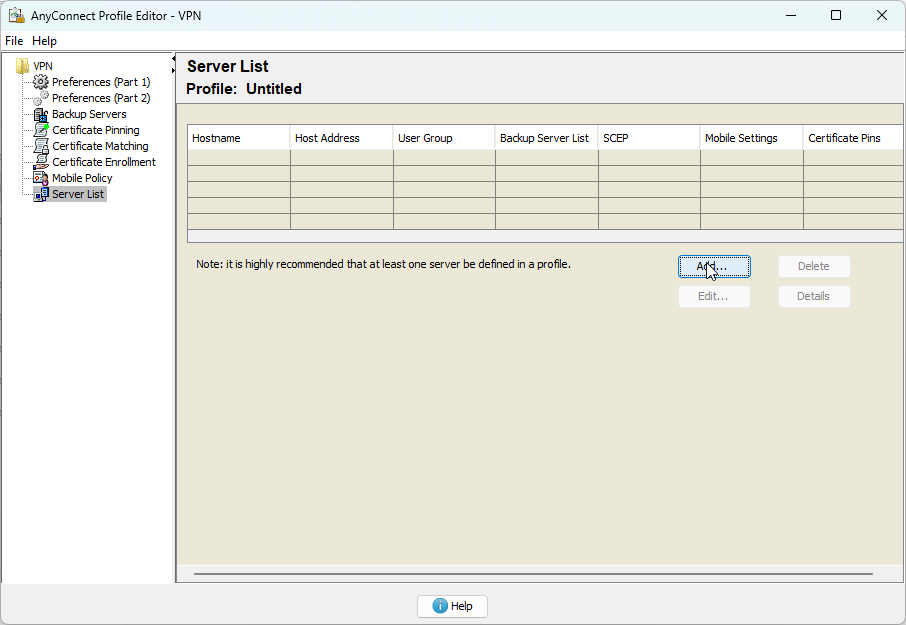
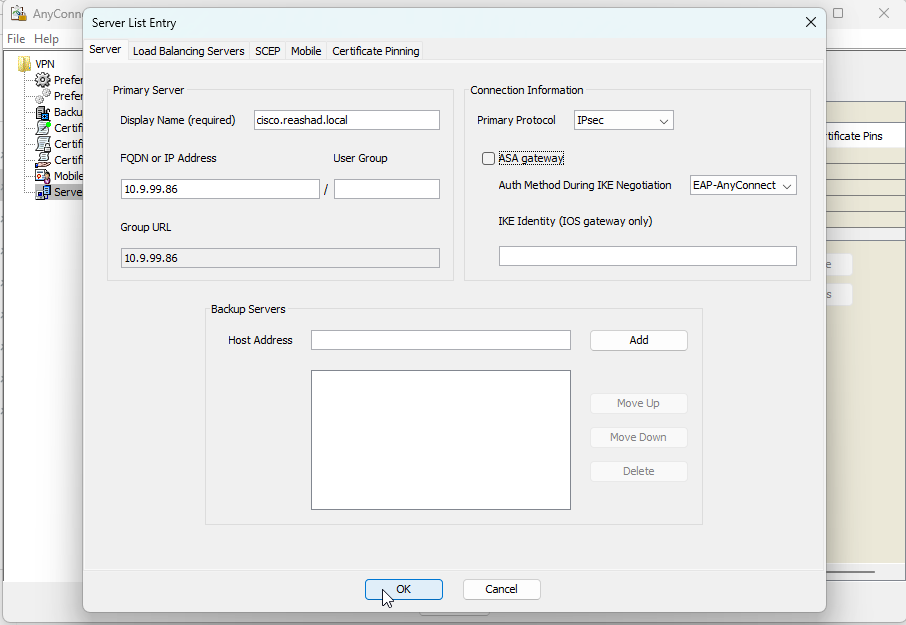
3. Save the profile and move it to C:ProgramDataCiscoCisco AnyConnect Secure Mobility ClientProfile
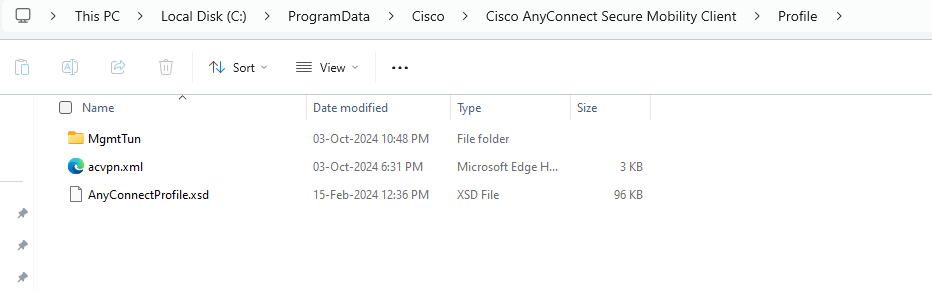
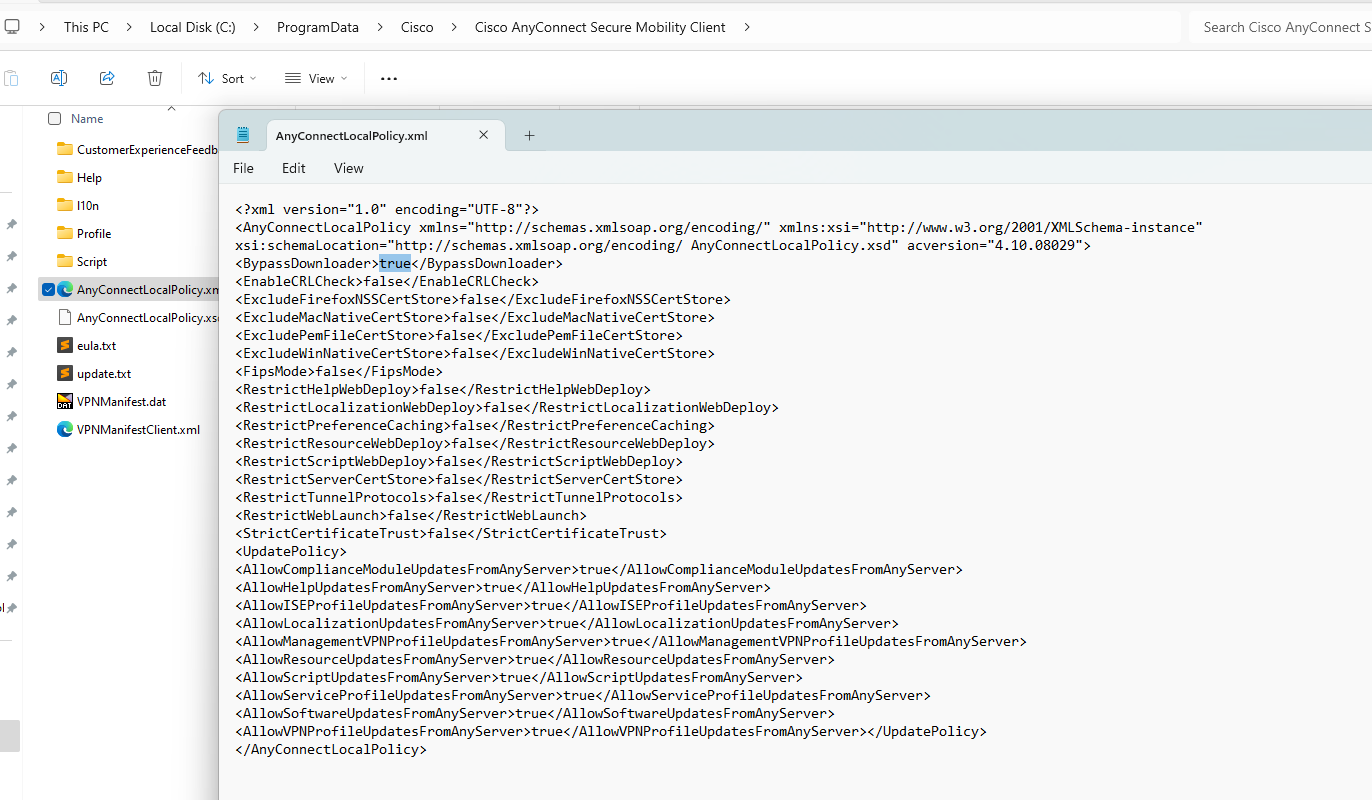
4.Open AnyConnectLocalPolicy.xml and edit BypassDownloader=true
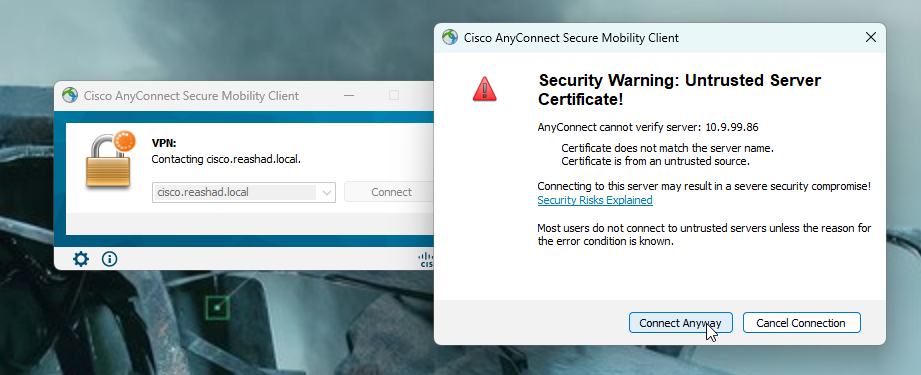
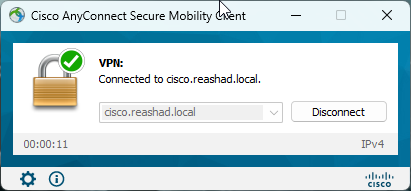
5.Open Anyconnect and connect to server

It has been broken down so well that anyone can follow!