Portfolio
80,000sqft warehouse design

Case summary
- This network was designed over 10+ years ago and never administered or maintained.
- Throughout Cat5 cables
- No port security resulted unauthorized BYOD trend
- Original designer left all ports om AUTO mode. This resulted uncontrollable network expansion without IT’s knowledge.
Design Phase 1
Let’s Discover!!!
- Found an old network diagram from the customer
- Diagram was created 10+ years ago and now it does not reflect the current setup. So physical cable tracing or LLDP discovery were the only 2 options to get more insight about this network.
- Check if LLDP was ON
- Yes, it was ON
- Checked with IT to see if they had IP address of the switches
- found some
- logged in to those devices and from LLDP neighbor table noted down the devices a switch it directly connected to.
- Found out IT only knows about 40% of the devices rest are unknown
- Used reverse ARP to find the other device’s IP.
- Logged into to those unknown devices and continued LLDP investigation
- Reached a point where I don’t see any more devices. Which meant (potentially!) I have discovered all the devices that are connected to my customers’ network.
- At this point I found over 50 switches connected to the network. Most of them are daisy chained. And there were so many single point of failures.
Design Phase 2
Analog to Digital
In this phase, I started creating proper Visio diagram.
Basically I just converted my pencil diagram to Microsoft Visio.
Design Phase 3
VLAN and config identification
In this phase I logged in to all the switches and tried to identify how they are configured like VLAN, DHCP relay, port aggregation any many more.
Design Phase 4
Redesign
This was the fun part of this project. At this phase I had all the information I needed to redesign a network.
- Carefully decommissioned bunch of unused VLANs any many more configuration.
- Introduced lots of security features, such as port security, root guard, port guard, DHCP snooping etc
- Decommissioned all the EOL devices and planned to purchase high port density Gigabit switches.
- Introduced longer username passwords
- disabled all the insecure protocols and introduced certificate based authentication
- Introduced Brute-force-Attack protection system
- At the end I planned to consolidate at network of 50+ switches to just 9 switches.
New Design
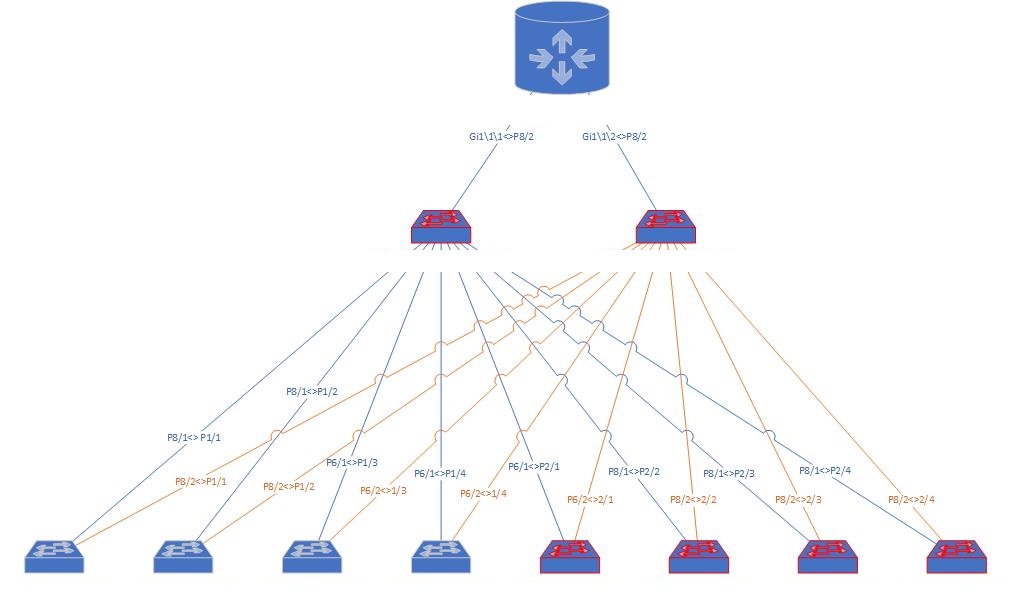
Design Phase 5
Call the Contractors and go shopping!
At this point called different contractors for laying out new cables and patch panels
- Obtained quotes from different cabling and patch panel companies and selected the most eligible one
- Ran over 29,000ft Cat6E cables
- Installed 200 patch panel ports and labeled them
- Ordered new switches from local partner
Design phase 6
Configure!
In this phase of this project all the new equipment came in. So I started pre-configuring them as per my design
Design Phase 7
All my bags are packed
I’m ready to go
I’m standin’ here outside your door…..
I was ready and the only thing was remaining was to find 2 consecutive non-productive days. So I communicated with the management and they provided me a weekend to migrate. The condition was on Monday when employees start to work, they shouldn’t notice any changes.
Basically this massive migration has to be transparent to the end users.
Final phase
Deployment
- Decommissioned over 50 old switches
- Rack mounted all the new switches
- Connected 200 cables to the new switch
- Connected 200 cables to the end user devices including PC, TV, printers.
- Tested and verified everything is working
This phase lasted for 2 days and each day I worked 17 hours straight. I had to do it otherwise on Monday warehouse’s conveyer belt wouldn’t run.
Handing over to the customer
after the successful deployment; I documented every possible little details and handed over the documentation to the customer.
All done.
Outcome of this project
- 1 Gbps access to core bandwidth
- superior network security by hard coding every ports and sticky MAC feature
- No scope for anyone to connect any unauthorized device.
- Proper documentation
- Redundancy
- Room for 15% future growth
- Disaster recovery plan
- network latency reduced by 30%
